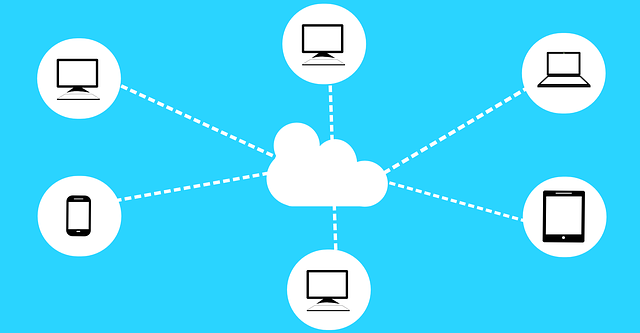
IoT software development is rapidly transforming our world. It can connect billions of devices and produce a surge of data. IoT offers a convenient and efficient future for everything from smart homes to industrial automation. But security is a major problem in this networked environment as well.
Security considerations are sometimes neglected in the process of creating cutting-edge IoT solutions. As a result, networks and devices may become targets of cyberattacks. This can have a devastating impact. In this article, we are going to examine the main security challenges that IoT software developers face. We have also crafted their effective solutions.
Security Concerns in IoT Software Development
The increasing popularity of IoT software development has raised serious security concerns. These devices frequently lack strong security measures. It leaves them vulnerable to a variety of cyber threats. Security attacks on IoT devices can have serious consequences. It includes privacy violations, financial losses, and even physical harm to individuals.
Common Security Challenges In IoT Application Development
Lack of Standardization
The lack of standardization in security protocols is one of the major challenges in IoT application development. Many manufacturers are producing IoT devices using various technologies and standards. This makes it difficult to maintain a consistent level of security throughout the ecosystem.
Vulnerabilities in Firmware and Software
A large number of security devices are functioning with out-of-the-date software and firmware. This leaves them open to known vulnerabilities. Such flaws grab the attention of hackers seeking to obtain access to your software. They can alter the functionality of your application or harm your devices.
Inadequate Authentication and Authorization Mechanisms
Another major security challenge in IoT software development is weak authorization and authentication protocols. Weak encryption techniques and insecure default passwords make it simpler for hackers to compromise IoT devices. Through these techniques, they can obtain unauthorized access to private information.
Overcoming Security Challenges
There is no doubt that IoT development provides a lot of benefits to its users, but there are also some challenges associated with it. Following are some measures that developers need to take in order to enhance the security of their devices.
Implementing Encryption Techniques
Strong encryption is required to protect data from unwanted access in transit and at rest. You can gain strong confidentiality by integrating your system with effective encryption methods. Methods like Secure Sockets Layer (SSL) and Advanced Encryption Standard (AES) can protect data integrity.
Regular Security Updates and Patches
It is essential to update software and firmware timetoregularly to address any issues. It also minimizes security flaws. Developers should set up systems for automatically updating security patches on devices on time. This helps to keep IoT devices safe from new threats.
Utilizing Secure Coding Practices
For IoT software to be secure and strong, secure coding practices must be implemented from the beginning of the development process. To find and fix common security flaws, developers should follow established security frameworks and guidelines, such as the OWASP IoT Top 10.
Role of AI and Machine Learning
AI and machine learning technologies have the potential to improve security in IoT software development. It facilitates early threat detection and mitigation.
Enhancing Security with AI-Driven Solutions
AI-driven solutions are capable of analyzing large data sets. These solutions help to find trends and abnormalities that could be signs of security threats. Developers can minimize the impact of cyberattacks by utilizing machine learning algorithms. Also, it detects and responds to security incidents in real-time.
Predictive Analytics for Threat Detection
AI predictive analysis has the ability to foresee any possible security concerns by utilizing behavioral patterns and historical data. Developers can effectively reduce risks and safeguard IoT devices from cyber threats. It detects and prevents any security vulnerabilities.
Ensuring Security and Regulatory Compliance in IoT Software Development
Collaborative Approach to Security
- Collaboration between developers, manufacturers, and cybersecurity experts is important. This helps in IoT application development to effectively address complex security challenges.
- Collaboration among stakeholders can streamline the process of identifying any security risks. It provides a collaborative environment to share threat intelligence, and put effective security measures in place.
- You can improve IoT ecosystem security by creating industry cooperation and best practice standards.
- Organizations can keep up with new threats and trends by exchanging threat intelligence and best practices. Also, they can catch up with new trends through programs like Information Sharing and Analysis Centers (ISACs).
Regulatory Compliance
- IoT software development must follow data protection regulations, such as the CCPA and GDPR. This promotes the ethical and responsible handling of user data.
- Following regulations is essential to prevent legal consequences and preserve user confidence. They impose strict limits on the gathering, handling, and retention of personal data.
- To ensure that they follow data protection laws, developers should give priority to implementing privacy. They should design principles and incorporate privacy controls into IoT software.
- Businesses can increase consumer confidence and foster trust in their IoT products and services by putting a high priority on data privacy and security.
Testing and Validation
IoT software development must include extensive testing and validation. It has a strong security approach to prevent any potential threat to the devices.
The Value of Examination: Thorough security testing helps device threats understand any security bugs or weak points in IoT devices in their early stages. Developers should integrate strong security postures into their hardware and software components. They should also perform code reviews, penetration tests, and vulnerability assessments.
Incorporating security testing:
All stages of the development lifecycle should incorporate security testing. Workflow efficiency depends on security measures, from design to post-deployment maintenance. Developers can reduce the risk in production environments by identifying and fixing them in the early stages. The integration of security testing into every stage of the development process saves a lot of time.
Conclusion
IoT software development security issues can cause a lot of damage to any company. Businesses must resolve these issues with a thorough and preventive strategy. This includes encryption, frequent updates, secure coding techniques, and AI-driven solutions. Moreover, teamwork, regulatory compliance, extensive testing, and user education greatly enhance the security of IoT devices.
Developers can improve the security posture of IoT devices by implementing strong security measures. They can meet these challenges directly and protect your application from potential cyber threats.