[ad_1]
Disasters can strike anytime without warning. The potential for significant disruption to businesses and communities is significant. This is where disaster recovery planning comes in. First we make sure that people and the overall environment are safe, and then the focus shifts to assessment and recovery efforts.
Recovery includes restoring critical infrastructure and operations in order to restore access to services. During the recovery process, the technology systems and data get recovered and we begin to move towards normal business operations following the disaster.
You must balance the importance of disaster recovery planning. According to a Disaster Recovery Preparedness Council study, 73% of companies have experienced a major disruption in business operations in the past five years. Of those, 40% never fully recover, and 25% fail within a year.
What are the keys to defining, documenting, and communicating a comprehensive disaster recovery plan, particularly for cloud-based applications?
What do we plan for?
It’s vitally important to understand disaster comes in many forms:
- Regional disruptions – power, network, local physical access to buildings which affects your access to your team’s resources or even your cloud provider’s resources.
- Global disruptions – singular causes that span a global, or extremely large area (e.g. Route 53 DNS outage affecting global DNS lookups).
- Individual and local disruptions – these are very localized issues that can be application-level, database-level, or somewhere within an organization’s configuration of their infrastructure or application.
The causes of any of these disruptions can be anything from natural environmental causes (e.g. storms, power loss, heat, flooding) to purely technical issues (e.g. connectivity, latency, human error, misconfiguration).
Your disaster recovery plan will likely document data backup and recovery procedures, alternative communication methods, and plans for restoring critical systems and infrastructure. The issue with most plans is that they tend to represent a point in time which is static and risks being out of date.
Knowing what to plan for is critical. It’s also equally important to understand why we need a plan to protect and recover our systems.
Ensuring Business Continuity and Resilience with Disaster Recovery Planning
In addition to complying with regulatory requirements, disaster recovery has many other benefits:
Provide business continuity – An effective disaster recovery strategy ensures that your business can continue operating despite unforeseen circumstances. Failure to have an effective DR plan can result in downtime, costing your business significant revenue and reputational impact.
Minimize downtime and data loss – The longer it takes for your business to resume to normal operations after an incident, the greater the risk of losing customers and falling behind competitors who can remain open or return to full availability quickly during disruption.
Safeguard against cyber threats – Cyber attacks and ransomware attacks are becoming more frequent, sophisticated, and effective. Disaster recovery planning can help you mitigate the risk of such attacks by giving you an established procedure for recovering your systems and data integrity in case of becoming compromised.
Enhancing customer trust and confidence – Customers rely on you to keep their information safe. Successful disaster recovery planning can demonstrate that you take their concerns seriously and have a solid plan if something goes wrong.
Improved disaster preparedness and risk management – Disaster recovery planning isn’t just about recovering from a disaster — it’s about preventing one from happening in the first place by reducing your company’s exposure to any threat to your service, application, and data availability.
Building a Strong Foundation: The Fundamentals of Disaster Recovery for IT Systems
Establishing a disaster recovery plan is important before a disaster occurs. The plan should contain the following elements:
Recovery Goals
The first step to effective disaster recovery planning is to define the goals and objectives of your disaster recovery strategy. Determine what kind of disaster recovery solution you need while identifying your organization’s goals.
The first goal is often communication infrastructure. This includes email, chat, and telephony. This is especially challenging with distributed teams. Luckily, many organizations have opted for SaaS services to provide communication access. This reduces the risk to the organization provided the SaaS service is not also affected by the disruption.
Personnel
Your DR strategy should include several layers of redundancy to ensure that employees can work from anywhere, anytime. Having the right people available and skilled for recovery processes is absolutely critical. It’s also important that these people are using systems and automation as much as possible to lower risk during recovery.
The IT recovery teams will need to have a deep understanding of what is required for any application to operate. This will depend on you having done a BIA (business impact analysis) and making the steps and prioritization of applications available before and during recovery.
IT Inventory and Dependency Mapping
Take a complete inventory of all hardware and software systems within your organization before developing any plan. This also comes from your BIA. You need this to help you to both protect and recover resources.
There should be a matrix of your core services, applications, and all dependencies. This helps you to define the order and requirements for each system to be recovered. This will be part of your recovery roadmap and will be heavily influenced by knowledge of both the business and systems.
Restoration (aka Backup) Procedures
Backups protect your IT systems if something goes wrong. They also allow you to restore data if necessary, which is important when recovering from disasters. In fact, the only reason we back systems up is to be able to restore them. This is why testing restores on a regular basis is of absolute importance.
You also need to understand how you will back up entire systems, partial systems, individual files, or even as granular as specific emails and database objects. You will require a variety of backup methods and each system or subordinate part of the system must be documented for protection and recovery.
Disaster Recovery Documentation and Procedures
Disaster recovery procedures are detailed instructions for what steps to take if there is an actual disaster. You also need to store and protect access to these procedures and documentation. That will be included in the oxygen services recovery which is the first layer of recovery.
The team will be able to use these procedures to recover and test systems in an orderly manner and restore availability.
🎥 Learn how to perform automated disaster recovery testing in this 5-minute video
Disaster Recovery Site Plans
A disaster recovery site is another location where you can bring up your IT systems in case they become unavailable at your primary location due to a natural or man-made disaster such as fire, flood, earthquake, etc.
Your DR site should be located at least 100 miles away from your primary location so that it doesn’t get affected by the same issues that affect it. This also gives your staff time to react before the event affects their commute home.
With public cloud services already available in a global network, this makes recovery of systems on the cloud much more accessible. You will be able to leverage the available alternate sites provided you have network and security access to the secondary locations.
The Application Recovery Plan
Your application recovery plans are the detailed steps needed to restore each application and their dependent systems.
Each application recovery plan will include a list of core components, dependencies, and test plans to let your team:
- Identify the failed component(s) – determine if the system can be recovered in place or must be moved to another location.
- Verify component availability – ensure all components required for operation are present and functional.
- Installing any missing components – reinstall or reconfigure components to return to availability post-disruption.
- Configuring any new components – some new components may be needed because you are in a recovery scenario (e.g. backup systems for your recovered environment).
- Testing the systems – ensure full operational availability before returning it to production use.
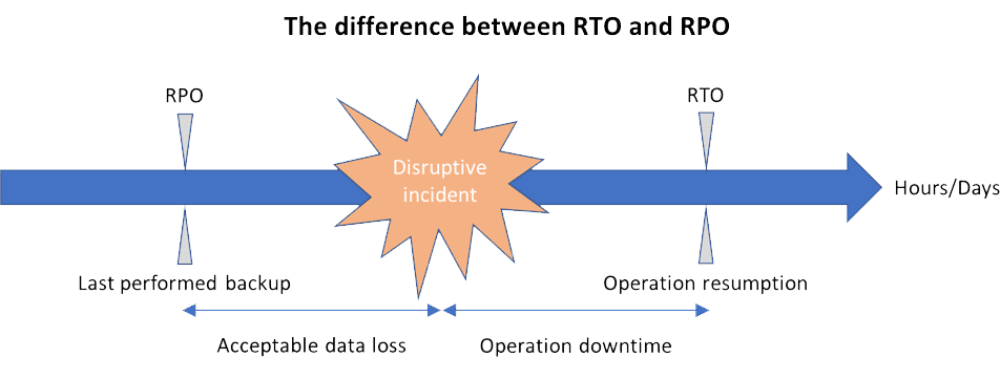
Understanding RTO and RPO: Key Differences and Importance in Disaster Recovery Planning
In disaster recovery planning, Recovery Time Objective (RTO) and Recovery Point Objective (RPO) are two crucial metrics.
RTO is the maximum amount of time a company can afford to be without a particular service or application following a disruption. It represents the time required to restore normal operations following a disaster. An organization must first identify the critical systems and applications that must be recovered in the event of a disruption to calculate RTO. Once the organization has identified the critical systems and applications, you can estimate the time required to recover each application and the dependent systems.
RPO represents the maximum amount of data loss an organization can tolerate following a disruption. It indicates the point in time to which data must get restored for operations to continue. To determine RPO, a business must first identify the crucial data that must get recovered in the event of a disruption. Once the organization has identified the critical data, it can estimate the amount of data that could get lost in the event of a disruption and the time by which they must restore the data.
To calculate RTO and RPO, an organization must conduct a comprehensive risk assessment and business impact analysis. This helps you to identify the critical systems, applications, and data and determine the potential business impact of a disruption. After identifying these factors, your team can develop a disaster recovery plan that includes RTO and RPO objectives. The plan should be reviewed and tested regularly to ensure that the RTO and RPO objectives are attainable and current.
The fundamental distinction between the two is their respective goals. While RTO assigns a time frame to viable strategic options that enable an organization to restart operations without using data, RPO measures the time that it can permit data to be lost and not how much data might get lost.
TIP: Learn how to get near-zero RTO sustainably in this post.
Resilience with Local and Cross-Region Protection Strategies
Choosing the right protection strategy is critical when protecting your business from threats such as natural disasters, cyber-attacks, and other disruptions. Two common options are local protection and cross-region protection.
Local protection involves implementing backups, redundant systems, and physical security at a single location. Conversely, cross-region protection involves replicating critical data and systems across multiple geographically dispersed locations, such as different data centers, even in different regions across the globe.
While both strategies can offer adequate protection, there are differences to consider. In the event of a widespread disaster that affects the entire region, local protection might be more effective and easier to manage. Cross-region protection offers greater resilience and redundancy but can be more complex and expensive.
Choosing between local and cross-region protection will ultimately depend on your organization’s specific needs and risk tolerance. It is important to assess your options carefully and work with experienced security professionals to develop your business’s most effective protection strategy.
Multi-cloud and Cross-Cloud for Resilience
Using multiple cloud providers to build a distributed system is referred to as multicloud or cross-cloud. The idea is to leverage the strengths of each cloud service provider and avoid vendor lock-in. This is an attractive concept but challenging to implement in practice.
The main reason for leveraging multicloud and cross-cloud services is because of a technical or business dependency on a specific cloud platform.
Let’s use the example of even a simple distributed web application. You may be able to benefit from cross-cloud architecture by distributing components such as the front-end, middle tier storage (e.g. key-value store (KVS), NoSQL, object storage), and back-end database across multiple cloud service providers.
You may have one system that maintains your source of record for client data, another that maintains vendor and partner resources, and more that are for internal operational applications and processes. This is another reason why multicloud recovery creates a challenge.
Both infrastructure (configuration, compliance, cost management, and security) and data management can differ wildly between cloud providers. This means you need to include many details about day-to-day operations in the recovery processes.
There are great advantages now with how much easier it is to get infrastructure up and running. This leads to the next area which is managing the safe state of the application.
Application and Data State Challenges During Recovery
One of the biggest challenges of a cross-cloud architecture is managing the application state and data state both in production and during recovery. When a distributed system component fails, the recovery process must ensure that we return the system to a consistent state.
In the case of our example distributed web application, the front end, middle tier, and database storage each have operational and recovery processes that will affect how you manage state. It may host the front end on one cloud service provider, the middle tier on another, and the database on another. This may seem complex but could be based on requirements of multiple applications being hosted that are dependencies for this top-level business application.
During recovery, someone must carefully manage the application state and data state. The application state includes any data stored in memory or caches, while the data state includes the state of the persistent storage, such as the database.
One challenge of managing the application state during recovery is that it may not be possible to recover the same state that existed before the failure. This is because it has lost the state due to failure, or must be inconsistent across different system components. The recovery process must ensure the application can recover gracefully by handling missing or inconsistent data to manage this challenge.
Managing data state during recovery is also challenging because the different components of the system may have different versions of the data. This can lead to inconsistencies and conflicts when the system is returned online. To manage this challenge, the recovery process must ensure that they reconcile the data across different system components to ensure consistency.
Conclusion
When it comes down to it, disaster recovery planning is about having a strategy for everything that could go wrong and understanding how to get back up if you do. This will include people, systems, data, and operational processes.
Your disaster recovery plan should have a deep understanding of RPO and RTO requirements for each of your applications, and the prioritization of recovery. Even the most thorough plan for infrastructure also needs to extend to understanding application state and how more modern distributed systems act during recovery.
Public cloud is a fantastic platform for hosting both production and disaster recovery but also requires an adaptive disaster recovery process and plan. Multicloud disaster recovery is also an interesting option with both advantages and challenges. No matter how you choose to host or recover your applications, an adaptive plan and tooling is a necessity for modern disaster recovery.
Automate Disaster Recovery Drills and Get Near-Zero RTO
N2WS Backup & Recovery makes it easy for you to put in place the most secure disaster recovery plans, to test them regularly (and get automated reports), and to recover in seconds to prevent downtime. You can try the Enterprise Edition of N2WS free for 30 days.
[ad_2]
Source link